Security
Articles
Allow arbitrary URLs, expect arbitrary code execution - Positive Security
Basic Linux Privilege Escalation - g0tm1k
Everything Public Key Infrastructure - Mike Malone
Free TryHackMe Training: The Ultimate Guide for Beginners - Ellie Gillard
Hack The Box (HTB) OSCP-Like machines List 2022 - PentestBlog
How To Become A Hacker - Eric Steven Raymond
Introduction to Ethical Hacking Live Training Guide - Omar Santos
Introduction to format string exploits - Code Arcana
Linux Privilege Escalation Using Capabilities - Heino Sass Hallik
Unofficial OSCP Approved Tools - FalconSpy
Penetration Testing Cheat Sheet - HighOn.Coffee
Privilege Escalation - Offensive Security
Reverse Shell Cheat Sheet - HighOn.Coffee
Reverse Shell Cheat Sheet - Pentest Monkey
Reversing for dummies - x86 assembly and C code - Sami Alaoui Kendil
Smashing The Stack For Fun And Profit - Aleph One
Smashing the Stack For Fun and Profit (Today) - Travis Finkenauer
Smashing the Stack for Fun & Profit: Revived - avicoder
So You Want to Be a Hacker: 2022 Edition - TCM Security
Starting an InfoSec Career - Lesley Carhart, tisiphone.net
Awesome
Blogs
Books
Computer Security: Principles and Practice - William Stallings, Lawrie Brown
Bug Bounty Programs
Certifications

A Guide to Information Security Certifications (2020 Update) - Daniel Miessler
Conferences
Databases
Metasploit Unleashed - OffSec
Systems and Network Hacking - Giuseppe Lettieri, Università di Pisa
Discords
Frameworks
GitHub Repositories
Cheatsheets - RedefiningReality
corkami/formats - file formats
corkami/pics - posters, drawings
hackingtool - ALL IN ONE Hacking Tool For Hackers
How To Secure Anything - Veeral Patel
Public Pentesting Reports - Julio Cesar Fort
Images

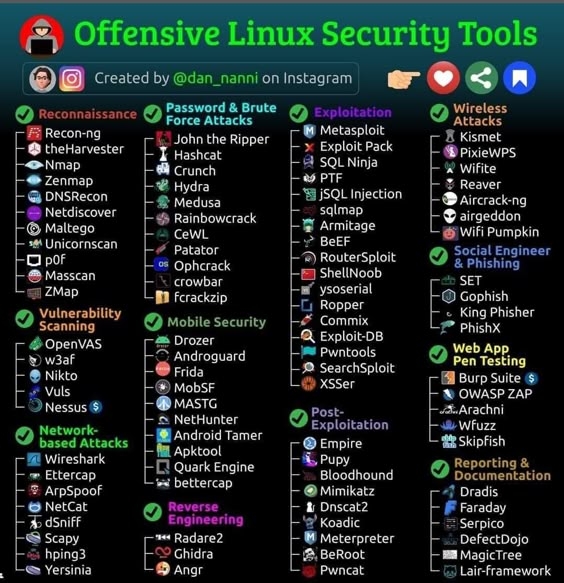

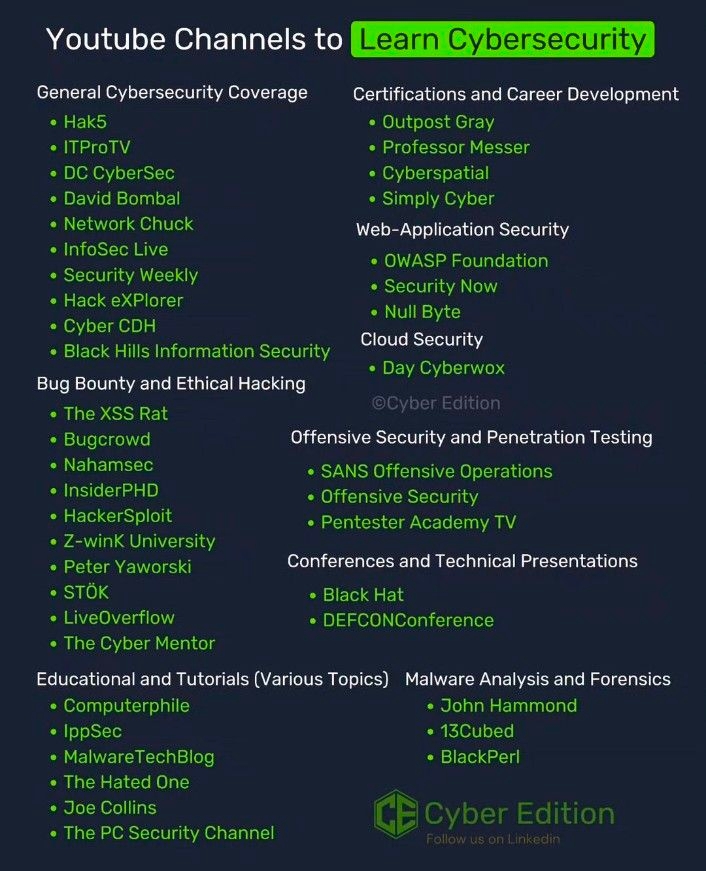
Linux Distributions
Kali Linux - OffSec
Parrot OS - Parrot Security
Meetups
Podcasts
Subreddits
Tools
BeRoot - Privilege Escalation Project
Dradis - Reporting and collaboration tool
DNSExfiltrator - Data exfiltration over DNS request covert channel
Ettercap - comprehensive suite for man in the middle attacks
GTFOBins - curated list of Unix binaries that can be used to bypass local security restrictions
Kaitai Struct - declarative binary format parsing language
LaZagne - Credentials recovery project
LinEnum - Scripted Local Linux Enumeration & Privilege Escalation Checks
Nessus - Vulnerability Assessment
Pupy - C2 and post-exploitation framework
SharpExfiltrate - Modular C# framework to exfiltrate loot over secure and trusted channels
Tails - Portable operating system that protects against surveillance and censorship
Unshackle - Password Bypass Tool
Videos
File Path Race Condition & How To Prevent It - LiveOverflow
How the Best Hackers Learn Their Craft - David Brumley
Introducing Pwncat: Automating Linux Red Team Operations - Caleb Stewart and John Hammond
Network Penetration Testing for Beginners (2019) - The Cyber Mentor
Websites
ANY.RUN - Interactive Online Malware Sandbox
crt.sh - Certificate Search
CyberDefenders - Online Cyber Security Blue Team Training
Deus x64 - A Pwning Campaign by RET2 Systems
Hacksplaining - Security Training for Developers
Have I Been Pwned - Check if your email has been compromised in a data breach
Kali Training - Mastering the Pentest Distribution
KC7 - A Cybersecurity Game
SANS - UK Cybersecurity Courses & Training
Security Certification Roadmap - Paul Jerimy
The Art of Hacking - Omar Santos
The Hacker News - #1 Trusted Cybersecurity News Platform
YouTube Channels
Chris Greer - Wireshark training
YouTube Playlists
Buffer Overflows Made Easy - The Cyber Mentor
Last updated